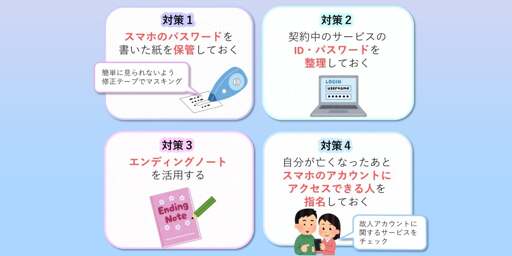
Japan’s National Consumer Affairs Center on Wednesday suggested citizens start “digital end of life planning” and offered tips on how to do it. The Center’s somewhat maudlin advice is motivated by recent incidents in which citizens struggled to cancel subscriptions their loved ones signed up for before their demise, because they didn’t know their usernames or passwords. The resulting “digital legacy” can be unpleasant to resolve, the agency warns, so suggested four steps to simplify ensure our digital legacies aren’t complicated:
- Ensuring family members can unlock your smartphone or computer in case of emergency;
- Maintain a list of your subscriptions, user IDs and passwords;
- Consider putting those details in a document intended to be made available when your life ends;
- Use a service that allows you to designate someone to have access to your smartphone and other accounts once your time on Earth ends.
The Center suggests now is the time for it to make this suggestion because it is aware of struggles to discover and resolve ongoing expenses after death. With smartphones ubiquitous, the org fears more people will find themselves unable to resolve their loved ones’ digital affairs – and powerless to stop their credit cards being charged for services the departed cannot consume.


Wait how does that work? I thought Bitwarden couldn’t access your passwords, how could they grant a third party access to your passwords without your master password?
my understanding is:
source