- 4 Posts
- 103 Comments

 3·30 days ago
3·30 days agoI took a look through the twitter, which someone mentioned in another thread.
Given the 4chan like aestetic of your twitter post, I decided to take a look through the boards and it only took me less than a minute to find the n word being used.
Oh, and all the accounts are truly anonymous, rather than pseudoanonymous, which must make moderation a nightmare. Moderation being technically possible doesn’t make it easy or practical to do.
I don’t want an unmoderated experience by default, either.
No, I’m good. I think I’ll stay far away from plebbit.

 3·30 days ago
3·30 days agoTo be pedantic, lemmy is federated, rather than decentralized (e.g. a direct p2p architecture).
With decentralization, moderation is much harder than federation, so many people aren’t a fan.

 1·1 month ago
1·1 month agoI’m not spotting it. “AI” is only mentioned once.
The key and secret in the docker compose don’t seem to be API keys, but keys for directus itself (which upon a careful reread of the article, I realize is not FOSS, which might be anpther reason people don’t like it").
Directus does seem to have some integration with openai, but it requires at least an api key and this blog post doesn’t mention any of that.
The current setup they are using doesn’t seem to actually connect to openai at all.

 2·1 month ago
2·1 month agoThere are a few reasons why I really like it being public, even though it means I have to be careful not to share sensitive stuff.
- It creates a portfolio for me (I’m an undergrad) because I document my projects on there
- When asking for help with certain complex things, it’s really easy to simply link to my blog, since I document almost everything I’ve tried and why it did or didn’t work. Here’s a recent example
- I can share cool stuff I have saved, like my lists of learning resources or lists of software, with others easily.

 4·1 month ago
4·1 month agoThis isn’t exactly what you want. But I use a static site generator, with a fulltext search engine (that operates entirely locally!), called quarto. (although there are other options).
Although I call it a “blog”, it really is more of a personal data dump for me, where I put all my notes down and also record all my processes as I work through projects. Whenever I am redoing something I know I did in an old project, or something I saved here (but disguised as a blogpost), I can just search for it.
Here is my site: https://moonpiedumplings.github.io/ . You can try search at the top right (requires javascript).

 2·1 month ago
2·1 month agoLol I misread it too.

 3·1 month ago
3·1 month agoThere is literally no way to do performant e2ee at large scale. e2ee works by encrypting every message for every recipient, on the users device.
At 1000 users, that’s basically a public room.

 5·1 month ago
5·1 month agoThere a source port of at least portal 1.
https://github.com/AruMoon/source-engine
Here’s the active fork of the original project. Going through the issues of the original project, it seems to have support for building for 64 bit platforms.
No portal 2 support though. Although mentioned in the issues of nileusr’s repo is this: https://github.com/EpicSentry/P2ASW , which is interesting

 4·1 month ago
4·1 month agoYou should look into “Configuration as code”, where you use automation via various methods and store the code in a git repo. The other commenter in the thread is a good example of this methodology, using Terraform and Ansible, but there are many ways to do this.

 21·1 month ago
21·1 month agoI think the mistake is they titled it “The last note taking app you’ll ever need” instead of “The last note taking app I’lll ever need”
Yes, seriously. The article seems to talk mostly about their personal usecases, which is fine. This app is great and it works for them. But it won’t work for everybody and the title should probably respect that instead of having a grating title that evokes a knee jerk reaction.
Databases are annoying it is legitimately more difficult to export data from a database to another, than it is to copy markdown notes from one folder to another. In addition to that, there are also tools that process markdown and do cool stuff with, like pandoc, beamer, revealjs, etc, which can’t really be done with the more opaque database format.
Also this notetaking service only appears to work while online. Again, fine for them — but a dealbreaker for many people.

 5·1 month ago
5·1 month agoAlright, this is gonna be long.
Firstly, yes, different static site generators have different templating langauges. But just like normal programming languages, it is easy to transition from one templating langauge to another. If you take a look at the syntax:
- Pelian: https://pypi.org/project/Jinja2/
- Hugo: https://pkg.go.dev/text/template, https://pkg.go.dev/html/template
Not drastically different, but reading the docs, they are all similar enough, and easy to learn.
I wouldn’t call go’s templating language “esoteric”, but it should be noted that jinja2 is has other uses, most notably it is the templating engine that Ansible uses.
As for the docs… This could probably be a blog post by itself.
Firstly, take a look at this website: https://killedbygoogle.com/ . Google has created and then killed 296 projects, many of which were actively used and working. Why?
This is because, internally at Google, you get promoted if you either A: write software, or B: add more features to software. So what happens is people write software, get promoted, and then realize they don’t get paid more if they actually maintain that software, so they just kill it. Also, they forget to write documentation (because it doesn’t pay more or get you promoted).
Hugo, is by a Google Engineer, and it shows (or at least, it used to). Software by Google has two distinct characteristics (actually 3 if we count being written in Go).
- It has every feature you could ever want, even stuff you haven’t heard of
- And it’s poorly documented. Or not at all lmao.
But, “being poorly documented” is not a permanent fixture of this software, but instead something that mostly persists for as long as it’s Google software. Often, these projects get “adopted” by the wider community, who fixes up their documentation. Looking at hugo’s docs, it doesn’t seem be nightmarishly bad, especially for the core, main set of features. Like the setup docs appear to be clear (although a more complex process than alternatives).
But like, for search options: https://gohugo.io/tools/search/ . That google software pattern continues. There are like 10 options on the page, and no docs from hugo on their usage/installation lol.
Anyway, I would recommend eithier Pelican or Jekyll, given your requirements. Because everything you write is in markdown, it will be fairly easy to move from one static site generator to another, even if you are dissatisfied.
Also, kinda sorta relevant:
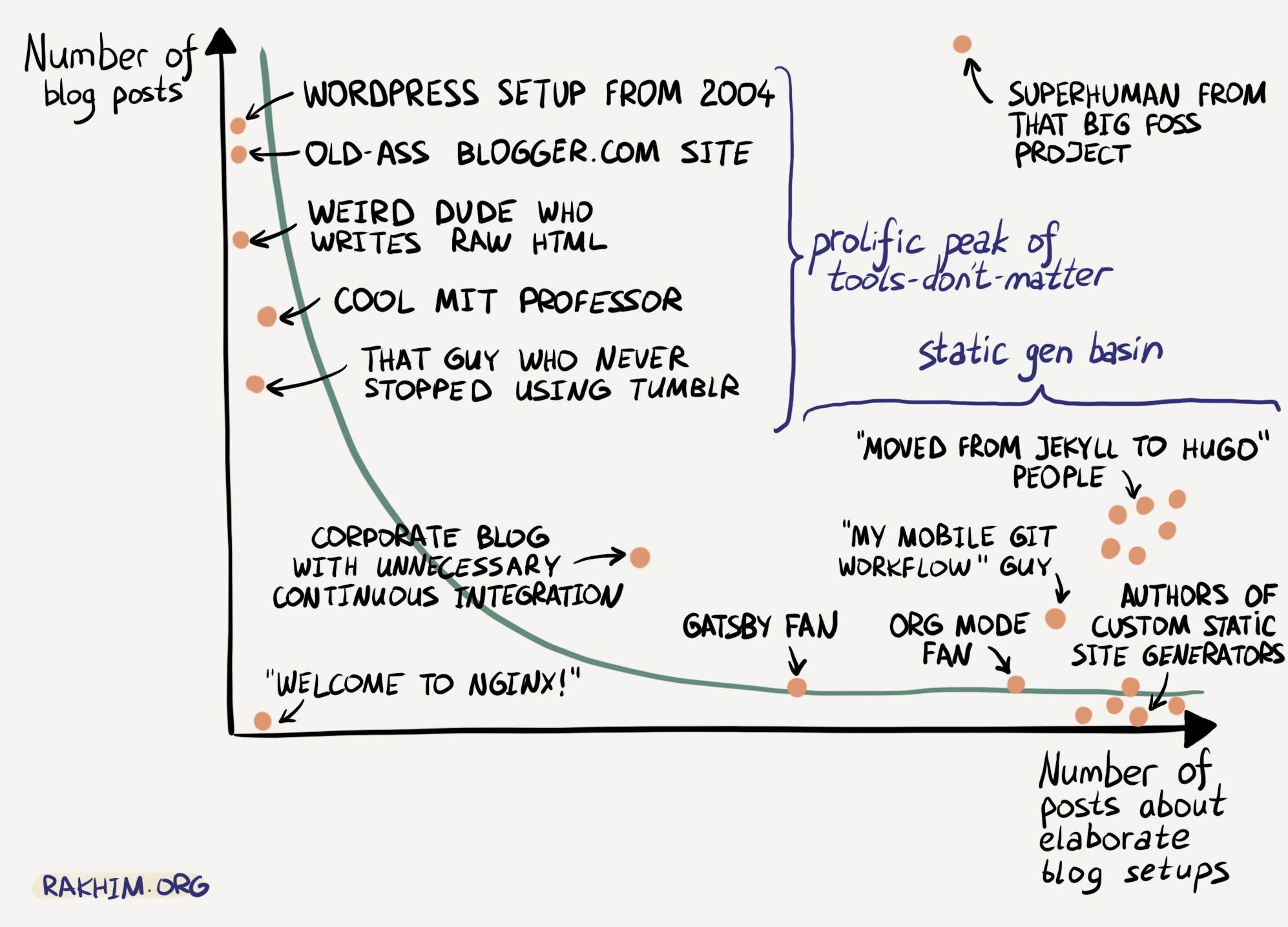
(source)
But the point I’m trying to make is the same. Don’t agonize over selecting the perfect static site generator.

 6·1 month ago
6·1 month agoI already made a comment but you should also look at rocketchat and revolt, since they are basically FOSS discord clones
(I saw comments in the thread about wanting audio only calls.)

 2·1 month ago
2·1 month agoIt’s actually not that hard. (Well it is, media and networking are hard, but)
I think the problem is that when people search for something better than Teams (or any other software), they confuse “better than”, with a mostly nonexistent “best”. In doing so, they skip over the way every single thing people suggest is “good enough”.
Like, following this thread, we went from “I want a teams (voice/video/chat) alternative” to “Yeah I don’t like Jami because it leaks metadata.” How did we go from wanting a teams alternative, to wanting privacy with no metadata leakage? Those are very different things, and you make tradeoffs if you take one set of feature over the other. If you just add “no metadata leakage” on top of your current wishes, then you are probably going to be disatisfied with every option given.
Or “Firewalls and hole punching!” (implying a p2p architecture) and “depends on peers being reliable” (being frustrated with the pitfalls of a p2p architecture). Again, wtf? Of course there is software that is both p2p and client server, but that is hard and tradeoffs will end up being made, even purely in what the developer spends their limited time on.
This person just needs to get out of their head, whip up deployments for every software (or suite if there is more than one) mentioned in the thread, and pick the one that looks the nicest.

 2·1 month ago
2·1 month agoQuarto has theming via several built in bootstrap themes.
Quarto is written in javascript.
Also, it has no template engine/templating. I have a nasty hack where I write python code blocks (vua quarto’s ability to execute code blocks) to output markdown that can be remdered to both html and pdf, which is pretty unique. But this is probably not what most people making a website want.

 3·1 month ago
3·1 month agoYou may want quarto. It is explicitly designed for data science and related usecases, and has ample support for the graphs those usecases need.

 6·1 month ago
6·1 month agoI use quarto: https://quarto.org/
The big thing I like is that it has fulltext local search, built in and easy to enable.
Search is possible on hugo, but it’s not built in, you have to get a plugin, etc etc. Same for many other options you mentioned.
Heres my website: https://moonpiedumplings.github.io/

 21·1 month ago
21·1 month agodeleted by creator

 231·1 month ago
231·1 month agoYou want either mattermost or the whole matrix stack (backend, plus element with voice/video calls).
Matrix/Element is more of a discord alternative, whereas mattermost tries to be more of a slack alternative, where it seems to have some calendar integrations.


Maybe nginx proxy manager can do this.
https://nginxproxymanager.com/